Discovering your accounts have been hacked can feel like someone broke into your digital home. When hackers gain access to your online accounts, they may steal personal data, send messages as you, or even steal your money. If you’ve been hacked, you should immediately change your passwords, scan your devices for malware, and monitor your accounts for suspicious activity.
The signs of being hacked aren’t always obvious. You might notice unusual emails sent from your account, strange social media posts you didn’t create, or unexpected password reset notifications. Sometimes, friends might tell you they’ve received strange messages from you, or you might find yourself locked out of your own accounts. Don’t panic—most hacked accounts can be recovered with the right steps.
Being hacked doesn’t mean you did something wrong. Even careful people can fall victim to sophisticated attacks. What matters most is how quickly you respond and what steps you take to secure your accounts afterward. With the right approach, you can minimize damage and better protect yourself in the future.
1. Recognize the Signs
You may be hacked if you notice:
- Unexpected password reset emails.
- Logins from unknown devices or locations.
- Strange messages sent from your accounts.
- New apps, software, or browser extensions you didn’t install.
- Slower device performance or pop‑ups.
(Source: Wired)
2. Act Immediately
🔑 Secure Your Accounts
- Change your passwords right away, starting with your email (since it controls most account recoveries).
- Use strong, unique passwords for each account.
- Enable two‑factor authentication (2FA) wherever possible.
📱 Lock Down Devices
- Disconnect from the internet if you suspect malware.
- Run a full antivirus or anti‑malware scan.
- Update your operating system and apps to patch vulnerabilities.
💳 Protect Financial Data
- Check your bank and credit card statements for suspicious charges.
- Contact your bank immediately if you see unauthorized activity.
- Consider placing a fraud alert or credit freeze with your credit bureau.
3. Recover & Restore
- Use account recovery tools (Google, Apple, Microsoft, etc. have dedicated recovery pages).
- Remove unknown devices or sessions from your account’s security settings.
- Reinstall or reset devices if malware is confirmed.
4. Prevent Future Hacks
- Use a password manager to generate and store unique passwords.
- Regularly update your devices and apps.
- Be cautious with links, downloads, and public Wi‑Fi.
- Back up your data to a secure location.
5. When to Get Help
- If you’re locked out of critical accounts (email, banking, work), contact the service provider immediately.
- If sensitive personal or financial info is exposed, report it to your bank and possibly local authorities.
- For workplace accounts, notify your IT/security team right away.
(Source: PCMag)
✅ Quick Checklist
- Change passwords & enable 2FA
- Scan for malware
- Monitor bank & credit accounts
- Review account activity
- Back up and update devices
Key Takeaways
- Change compromised passwords immediately and enable two-factor authentication on all your accounts.
- Run security scans on your devices and watch for unusual activity in your financial accounts.
- Create unique, strong passwords for each account and be cautious about sharing personal information online.
Understanding the Threat of Getting Hacked
Getting hacked isn’t just a risk for large companies – it affects individuals every day. Hackers use increasingly sophisticated methods to gain access to personal data, financial information, and digital devices.
Cybercrime Landscape
The digital threat landscape has evolved dramatically in recent years. Hackers are unauthorized users who break into computer systems to steal information or cause damage. They vary greatly in their skills and motivations.
Some hackers are simply looking to cause mischief, while others have more sinister goals. Professional cybercriminals target individuals and businesses for financial gain through identity theft or financial fraud.
State-sponsored hackers work for governments to steal secrets or disrupt critical infrastructure. Hacktivists break into systems to promote political causes or ideologies.
The costs of cybercrime continue to rise each year. When you’re hacked, you might face financial losses, identity theft, or the exposure of private information.
Common Hacking Techniques
Hackers use various methods to gain unauthorized access to your devices and accounts. Phishing emails remain one of the most common tactics, where attackers send fake messages that appear to come from legitimate sources to trick you into revealing sensitive information.
Common hacking methods include:
- Malware – harmful software like viruses and trojans that damage your system
- Ransomware – programs that lock your files until you pay a ransom
- Social engineering – psychological manipulation to trick you into revealing information
- Password attacks – attempts to guess or crack your login credentials
Many attacks begin with simple tricks rather than complex technical exploits. A hacker might call pretending to be tech support or send an email that looks like it’s from your bank.
Once they gain access, hackers can steal your personal data, install spyware to monitor your activities, or use your computer in larger attack networks.
How Hackers Access Your Information
Hackers use several methods to steal your personal data, often targeting the weakest link in security systems. They constantly develop new techniques to bypass protection measures on your devices.
Exploits in Software and Hardware
Hackers frequently target unpatched software to gain access to your information. When you delay updating your computer, smartphone, or other devices, you leave security holes open for attackers.
These vulnerabilities exist in many places:
- Operating systems (Windows, Mac)
- Web browsers
- Email clients
- Smart TVs and other connected devices
Hardware-based attacks are less common but still dangerous. Hackers might install keyloggers—physical devices attached to your laptop that record every keystroke, including passwords and personal information.
Public charging stations can pose risks too. Hackers modify these to extract data from your phone while it charges, a technique called “juice jacking.”
The Role of Social Engineering
Social engineering attacks target human psychology rather than technical vulnerabilities. Hackers manipulate you into revealing sensitive information or performing actions that compromise security.
Common social engineering tactics include:
Pretexting: A hacker creates a fabricated scenario to obtain information. For example, someone calls pretending to be from your bank’s fraud department.
Baiting: Attackers leave infected USB drives in public places, hoping you’ll plug them into your computer out of curiosity.
Hackers gather information from social media to make their attacks more convincing. Those vacation photos you posted might reveal when your home is empty or provide answers to security questions.
Phishing: The Persistent Threat
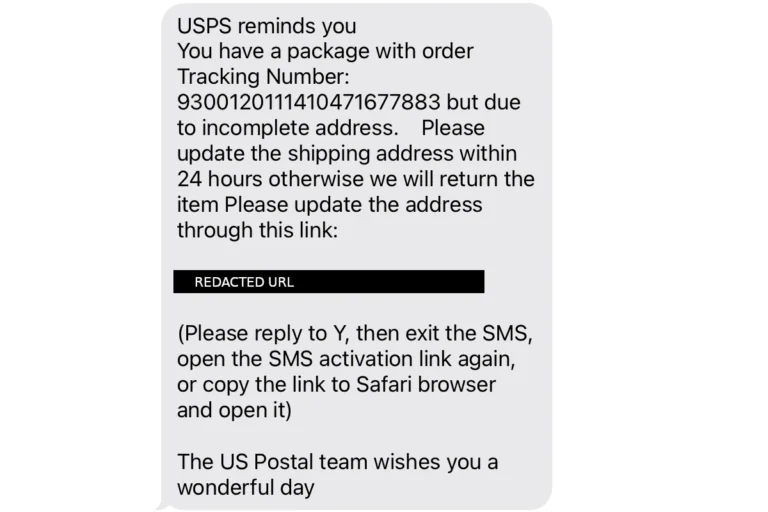
Phishing remains one of the most common ways hackers steal passwords and personal information. These attacks typically arrive via email but can also come through text messages or social media.
A typical phishing attempt includes:
- An urgent message claiming to be from a trusted source (your bank, Microsoft, etc.)
- A request for immediate action
- A link to a fake website designed to look legitimate
These fake sites can perfectly mimic real login pages for banks, email providers, or shopping sites. Once you enter your credentials, hackers capture them immediately.
Advanced phishing techniques include clickjacking and waterhole attacks. In clickjacking, transparent elements overlay legitimate websites, capturing your clicks. Waterhole attacks compromise websites you frequently visit, infecting your devices when you return.
Personal Data Protection
Protecting your personal data online requires proactive measures to prevent unauthorized access. The following strategies can significantly reduce your risk of being hacked or having your information compromised.
Essentials of Strong Passwords
Creating strong passwords is your first line of defense against hackers. A strong password should be at least 12 characters long and include a mix of uppercase letters, lowercase letters, numbers, and special characters.
Never use obvious information like birthdays, names, or common words. These are easily guessed by both humans and password-cracking software.
Consider using password managers to generate and store complex passwords securely. These tools create random, unique passwords for each of your accounts, so you don’t have to remember them all.
Change your passwords regularly, especially for sensitive accounts like banking and email. Experts recommend updating them every 3-6 months.
Most importantly, use different passwords for different accounts. This prevents a single breach from compromising all your online accounts.
Importance of Multifactor Authentication
Two-factor authentication (2FA) or multifactor authentication (MFA) adds an essential extra layer of security beyond just passwords.
With MFA, you’ll need to provide at least two forms of verification: something you know (password), something you have (phone or security key), or something you are (fingerprint or face scan).
Even if hackers obtain your password, they still can’t access your account without the second verification method. This dramatically reduces your risk of being hacked.
Many services now offer MFA options, including:
- Text message codes
- Authentication apps (Google Authenticator, Authy)
- Security keys (YubiKey)
- Biometric verification
Enable MFA on all accounts that offer it, especially financial, email, and social media accounts.
Securing Personal Devices and Networks
Your devices and home network require specific security measures to protect your data.
Keep all devices updated with the latest security patches and software versions. Manufacturers regularly release updates that fix security vulnerabilities.
Install reputable antivirus and anti-malware software on all devices. Schedule regular scans to detect and remove potential threats.
Be cautious when using public Wi-Fi networks, as they’re often unsecured. Avoid accessing sensitive accounts or sharing personal information when connected to public networks.
Consider using a Virtual Private Network (VPN) when browsing public internet. VPNs encrypt your connection, making it difficult for others to intercept your data.
Secure your home Wi-Fi with a strong password and WPA3 encryption if available. Change the default router login credentials and keep your router firmware updated.
Responding to Data Breaches
When your systems get hacked, quick and effective response can mean the difference between minor disruption and major disaster. Knowing exactly what steps to take after discovering a data breach helps protect your sensitive information and limit potential damage.
Detecting a Data Breach
Data breaches often go unnoticed for weeks or even months. Watch for unusual signs like unexpected account lockouts, missing funds, or strange computer behavior. Install monitoring tools that alert you to unauthorized access attempts or unusual data transfers.
Many breaches are discovered when customers report suspicious activity. Set up automated alerts for large data transfers or after-hours system access. Regular security audits can help catch breaches early by identifying vulnerabilities.
The average breach takes over 200 days to detect, so implementing continuous monitoring is crucial. Don’t ignore warning signs like slow network performance or unusual error messages—these might be your first clues of a breach.
Immediate Actions Post-Breach
Once you confirm a breach, act quickly to contain the damage:
- Isolate affected systems to prevent further data loss
- Document everything from the moment of discovery
- Notify your IT security team or hire external experts
- Change all passwords immediately
Following the 72-hour response guidance can help structure your initial actions. Don’t shut down systems completely, as this might destroy valuable evidence needed for investigation.
Determine what data was compromised. Was it customer information, financial records, or intellectual property? This helps assess your legal obligations regarding notifications.
Begin preparing communications for affected parties. Transparency builds trust, even during a crisis. Follow regulatory requirements for reporting data breaches to authorities.
Mitigation and Recovery Strategies
After containing the immediate threat, focus on fixing vulnerabilities and preventing future breaches:
Recovery Steps:
- Restore systems from clean backups
- Patch security holes that allowed the breach
- Install additional security measures
- Monitor for any lingering unauthorized access
If the breach exposed personal information, provide affected individuals with identity theft protection services. Advise them to place a credit freeze on their accounts and check their credit reports regularly.
Conduct a thorough post-breach analysis to understand how it happened and what you can improve. Update your security protocols based on lessons learned. Consider implementing better cybersecurity practices like regular software updates, safe browsing training, and stronger authentication.
Remember that recovery is ongoing. Continue monitoring systems vigilantly for months after the incident to ensure the attackers haven’t left behind backdoors.
Frequently Asked Questions
Getting hacked can be scary, but knowing how to respond can help you regain control quickly. These common questions address the immediate steps you should take when facing different types of security breaches.
What steps should be taken if one suspects their Facebook account has been compromised?
If you think your Facebook account has been hacked, change your password immediately. Choose a strong, unique password that you don’t use for other accounts.
Report the unauthorized access to Facebook through their help center. This helps Facebook track the issue and potentially restore your account faster.
Check your account activity to see if any posts, messages, or friend requests were sent without your knowledge. Delete any suspicious content and alert friends not to click on strange links that may have been sent from your account.
How can an individual recover from a hacking incident involving multiple personal accounts?
Start by making a list of all affected accounts and prioritize them based on sensitivity. Financial accounts should be addressed first, followed by email, then social media.
Use a different device than your potentially compromised one to change all passwords. Create unique passwords for each account or consider using a password manager.
Enable two-factor authentication on all accounts that offer it. This adds an extra layer of security by requiring a second verification step beyond just your password.
Contact customer support for accounts you can’t access. Most services have specific recovery processes for hacked accounts.
What are the initial symptoms indicating a possible security breach in one’s online presence?
Unexpected password reset emails are a major red flag. If you receive notifications about password changes you didn’t request, your account may be compromised.
Strange device behavior like unusual battery drain, overheating, or apps crashing frequently could indicate malware. Your device might also run noticeably slower than normal.
Unexplained account activity such as posts you didn’t create, emails in your sent folder you didn’t send, or unfamiliar transactions are clear signs of a breach.
Friends receiving messages from you that you never sent is another common indicator of compromise.
What actions should be immediately executed following the hacking of a social media account?
Change your password right away and log out of all sessions. Most platforms allow you to see active sessions and force-logout from unknown devices.
Check and revise your account privacy settings. Hackers often change these to gain more access or visibility to your information.
Review and remove any unauthorized apps or connections to your account. Third-party apps with account access can be used as backdoors by hackers.
Contact the platform’s support team to report the hack and get additional help. Many social networks have specific procedures for hacked accounts.
What are the recommended precautions after experiencing unauthorized access to a Gmail account?
Run a Security Checkup through Google’s security tools. This helps identify suspicious activity and secure vulnerable areas of your account.
Review and remove any email forwarding rules or filters that may have been set up. Hackers often create these to secretly receive copies of your emails.
Check your recovery email and phone number to ensure they haven’t been changed. Update them if necessary to maintain control of recovery options.
Review third-party apps with access to your Gmail and revoke permissions for any you don’t recognize or need. Unnecessary connections increase your risk.
How can one effectively secure their digital information against potential hacking attempts?
Use strong, unique passwords for every account and consider a password manager to keep track of them. Lengthy passwords with a mix of characters provide better protection.
Enable two-factor authentication wherever possible. This additional verification step makes it much harder for hackers to access your accounts, even if they obtain your password.
Keep all devices and software updated. Security patches fix vulnerabilities that hackers can exploit, so install updates promptly when they become available.
Be cautious about phishing attempts in emails, texts, and calls. Never click suspicious links or provide personal information unless you’re certain of the legitimacy of the request.
Regularly back up important data to secure locations. This ensures you can recover your information if ransomware or other attacks compromise your primary devices.