Phone hacking poses a serious threat to personal privacy and security and users often wonder if there’s a secret code to check if their device has been compromised. While no single code can definitively prove hacking, several codes can reveal potential signs of unauthorized access or tampering.
One useful code is *#06#, which displays the phone’s IMEI number. This unique identifier should match the one on the device’s packaging or settings menu. A mismatch could indicate tampering. Other codes like *#62# and *#67# check call forwarding settings, potentially revealing if calls are being redirected without the owner’s knowledge.
Users can also dial *#21# to view all diverted call settings at once. Unexpected forwarding numbers or settings may signal unauthorized access. It’s important to note that while these codes can provide valuable information, they are not foolproof methods for detecting all types of hacking or surveillance.
Codes To Check Your Phone
There is no single “secret code” that will definitively tell you if your phone is hacked. However, there are certain codes and methods you can use to check for signs of unusual activity or potential security breaches:
1. Check for Unusual Activity
- Unexpected data usage: Monitor your data usage for any spikes or unusual patterns.
- Unfamiliar apps: Look for apps you don’t recognize or remember installing.
- Strange phone behavior: Pay attention to unexpected reboots, pop-up ads, or battery drain.
- Suspicious messages: Be wary of messages from unknown numbers or with unusual content.
2. Use Codes to Access Information
- *#06#: This code displays your IMEI number. Compare it with the number on your phone’s packaging or in your device settings. A mismatch could indicate a cloned device.
- *#21#: This code can reveal if your calls, messages, or data are being forwarded to another number.
- *#62#: This code shows where your calls are being forwarded if your phone is unreachable.
3. Check Your Phone’s Settings
- Installed apps: Review the list of installed apps and remove any you don’t recognize.
- App permissions: Check the permissions granted to your apps and revoke any unnecessary ones.
- Security settings: Ensure your phone’s security features are enabled, including screen lock, biometric authentication, and encryption.
4. Install Security Software
- Antivirus apps: Use reputable antivirus apps to scan for malware and other threats.
- Anti-spyware apps: Consider using anti-spyware apps to detect and remove spyware.
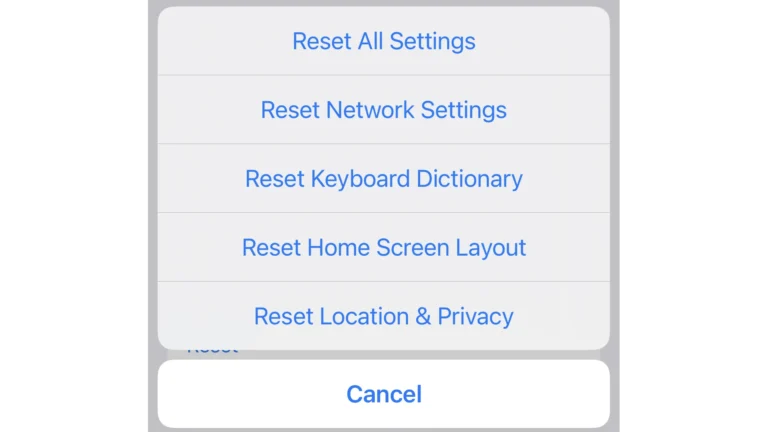
5. Factory Reset
- If you suspect your phone is hacked, a factory reset can remove malicious software and restore your phone to its original settings. Remember to back up your data before performing a reset.
Important Notes
- No code guarantees detection: These codes and methods can provide clues, but they don’t guarantee the detection of all types of hacking.
- Stay vigilant: Be cautious with what you download, click on, and share online.
- Keep your software updated: Regularly update your phone’s operating system and apps to patch security vulnerabilities.
- Use strong passwords: Choose strong, unique passwords for your accounts and enable two-factor authentication whenever possible.
Key Takeaways
- No single code definitively proves phone hacking, but several can reveal potential signs
- IMEI and call forwarding codes help check for unauthorized changes to device settings
- Regular checks using these codes should be part of a broader mobile security strategy
Understanding Phone Hacking and Security Risks
Phone hacking and cyberattacks pose serious threats to mobile device users. Recognizing the signs of a compromised phone is crucial for protecting personal information and data.
Defining Phone Hacking and Cyberattacks
Phone hacking refers to unauthorized access to a mobile device’s data or functions. Cybercriminals use various methods to breach phone security, including malware, phishing, and exploiting software vulnerabilities. Common goals of hackers include stealing personal information, accessing financial accounts, and spying on communications.
Cyberattacks targeting phones can take many forms. Some involve tricking users into downloading malicious apps or clicking on harmful links. Others exploit weaknesses in operating systems or network connections. Sophisticated attacks may even use fake cell towers to intercept calls and messages.
Signs That Your Phone Is Hacked
Several indicators may suggest a phone has been compromised:
- Rapid battery drain
- Unexpected data usage spikes
- Strange noises during calls
- Unfamiliar apps or icons
- Unusual text messages or emails
Performance issues like slow operation or frequent crashes can also signal a problem. Users might notice their phone turning on or off by itself. Suspicious activity on personal accounts linked to the device is another red flag.
Some telltale signs are more technical. Unexplained call forwarding or strange phone numbers in the call log may indicate hacking. Unusual background noise or echo during calls can suggest eavesdropping.
Analyzing Your Phone’s Vulnerabilities
Mobile devices face various security risks. Understanding these vulnerabilities helps users protect their phones from potential hacks and unauthorized access.
The Role of IMEI Numbers in Security
The International Mobile Equipment Identity (IMEI) is a unique 15-digit code assigned to every mobile device. This number serves as a digital fingerprint for your phone. To check your IMEI, dial *#06# on your device.
A changed IMEI may indicate a compromised phone. Hackers sometimes alter this number to mask stolen devices. Regularly verifying your IMEI helps detect unauthorized modifications.
Keep your IMEI private. Sharing it could allow others to clone your phone or track your location.
Firmware and Software Integrity Checks
Firmware acts as the foundational software of your device. Hackers may exploit vulnerabilities in outdated firmware versions.
To check your phone’s camera firmware details on Android, dial ##34971539##. This code reveals hardware information and recent camera usage.
Regular software updates patch security holes. Enable automatic updates to stay protected. Be cautious of unfamiliar apps, as they may contain malware.
Unexpected changes in system behavior or performance often signal compromised software integrity.
Unknown Connections and Data Forwarding Risks
Unauthorized data forwarding poses a significant threat to phone security. Hackers use this method to intercept calls and messages.
To check call forwarding status, dial *#21#. This code shows if your calls are being redirected without your knowledge.
Monitor your data usage closely. Sudden spikes may indicate malicious activity. Check your MAC address by dialing *#232338# on Android devices.
Unusual network connections or unfamiliar Wi-Fi networks could be signs of hacking attempts. Use caution when connecting to public networks.
Methods to Check for Hacking and Redirection
Several techniques can help users detect if their phone has been compromised or if calls are being redirected. These methods involve using special codes and checking call forwarding settings.
Using USSD Codes to Check Security
USSD (Unstructured Supplementary Service Data) codes allow users to access hidden menus and perform security checks on their phones. To check for potential hacking, users can dial *#21# on their phone’s keypad. This code reveals if call forwarding is active and displays any numbers set for redirection.
Another useful code is *#62#, which shows if calls are being forwarded when the phone is unreachable. For a comprehensive check, *#004# displays all call diversion settings at once.
Android users can use ##1472365## to verify their GPS location. This helps detect if location tracking has been compromised.
Identifying and Analyzing Conditional Call Forwarding
Conditional call forwarding redirects calls under specific circumstances. To check for this, users can dial *#67#. This code shows if calls are being forwarded when the line is busy.
The code *#61# reveals if unanswered calls are being redirected. Users should pay attention to any unfamiliar numbers listed in these settings.
If any suspicious forwarding is found, users can disable it by dialing ##002# to cancel all diversions. It’s important to regularly check these settings to ensure call privacy and security.
For iPhone users, additional checks can be performed through the Settings app under Phone > Call Forwarding. This provides a user-friendly interface to manage call redirection settings.
Remediation and Prevention Strategies
Protecting your smartphone from hacking requires a multi-faceted approach. Effective strategies include resetting devices, using security software, and implementing ongoing protective measures.
When and How to Perform a Factory Reset
A factory reset can be a powerful tool to remove malware and restore your phone to its original state. To perform a reset on most Android devices, go to Settings > System > Reset options > Erase all data (factory reset). For iPhones, navigate to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
Before resetting, back up important data to avoid loss. After the reset, set up your phone as a new device rather than restoring from a backup to prevent reintroducing malware.
Factory resets are recommended if you suspect a hack, notice unusual behavior, or plan to sell your device. However, they should be a last resort due to data loss.
The Importance of Antivirus Software
Antivirus software acts as a crucial defense against malware and hacking attempts. Top-rated options like TotalAV offer real-time protection, scanning incoming files and apps for threats.
These programs can:
- Detect and remove malware
- Block malicious websites
- Alert you to potential security risks
Many antivirus apps also include additional features like VPNs and password managers, enhancing overall device security.
Regular updates are essential to maintain effectiveness against new threats. Set your antivirus to update automatically for the best protection.
Monitoring and Protecting Your Smartphone
Active monitoring helps detect and prevent hacking attempts. Regularly check your phone for:
- Unusual battery drain
- Unexpected data usage
- Strange noises during calls
- Unfamiliar apps or processes
Enable built-in security features like:
- Two-factor authentication
- Biometric locks (fingerprint or face recognition)
- Find My Device (Android) or Find My iPhone (iOS)
Keep your operating system and apps updated to patch security vulnerabilities. Only download apps from official stores and be cautious with app permissions.
Use strong, unique passwords for all accounts and consider a password manager to help manage them securely.
Frequently Asked Questions
Phone security is a critical concern for many users. These questions address common issues related to detecting and addressing potential hacking or surveillance on mobile devices.
How can I determine if my phone has been compromised?
Look for unusual behavior on your device. Rapid battery drain, unexpected app installations, and slow performance can indicate potential hacking. Check your phone’s IMEI number by dialing *#06#. If it differs from the usual number, your device may be compromised.
What steps should I take to remove a hacker from my phone?
Start by updating your phone’s operating system and apps. Remove any suspicious applications. Change all your passwords, especially for sensitive accounts. Consider performing a factory reset if the problem persists.
Are there any special codes for Android devices to check for hacking?
Android devices have several diagnostic codes. *#21# checks for call forwarding, which hackers might use to intercept calls. *#62# verifies if any calls are being diverted when your phone is unreachable.
Is there a specific code for Samsung phones to verify if they are hacked?
Samsung phones use similar codes to other Android devices. *#9900# accesses a diagnostic menu that can reveal unusual system activity. However, interpretation of this data may require technical expertise.
How can one verify if their phone is under surveillance?
Check for high data usage when the phone is idle. Listen for background noise during calls. Look for unexpected text messages with random characters, which could be control codes for spyware.
Can dialing *#21 reveal if my phone’s security is breached?
Dialing *#21# shows call forwarding settings. While it doesn’t directly indicate hacking, unexpected call forwarding could suggest unauthorized access to your phone. Always verify these settings periodically.